Conceptual Framework of IoT-based Door Access Using Face Recognition
This post will demonstrate how to develop a conceptual framework for a capstone project called IoT-based Door Access using Face (Python. The study’s conceptual framework was built using the input, process, and output (IPO) model.
About the Project
Table of Contents
The Internet of Things (IoT) has revolutionized the way we interact with everyday objects and devices, making our lives more efficient and convenient. One of the many applications of IoT is in the realm of access control, which has been greatly enhanced by integrating facial recognition technology. IoT-based door access control systems leverage the power of the internet and interconnected devices to enhance security and convenience. Facial recognition technology, a subset of biometrics, has gained popularity in access control systems due to its accuracy and ease of use. This technology allows you to grant or deny access to individuals based on their facial features, making it a secure and efficient method for controlling entry into buildings, homes, or restricted areas. IoT-based door access control systems using facial recognition are a powerful combination of modern technology, offering enhanced security and convenience. With Python as your programming language, and a Raspberry Pi as the central component, you can create a cost-effective and versatile solution for controlling access to your home, office, or any secure area. This project is a great way to learn more about IoT, facial recognition, and Python programming while also enhancing security in your environment.
Objectives of the Study
General Objective: The research study aims to develop an advanced IoT-based Door Access System employing Face Recognition technology, contributing to enhanced security measures and seamless access control in various environments.
Specific Objectives:
- To design and implement a robust face recognition mechanism that accurately identifies and grants access to authorized individuals, ensuring a secure and efficient door access system.
- To integrate IoT sensors and network connectivity, enabling real-time monitoring and remote access control for administrators and security personnel, ensuring comprehensive oversight and management of access permissions.
- To enhance the user experience by developing a user-friendly interface for easy enrollment of authorized users, providing streamlined access management and user authentication processes.
- To assess and enhance the system’s reliability and security features through continuous testing and evaluation, ensuring the system’s effectiveness in preventing unauthorized access and safeguarding sensitive areas.
What is a Conceptual Framework?
A Conceptual Framework is a structured outline that defines the fundamental concepts, objectives, and methodologies essential for guiding a research project or capstone initiative, such as the development of an IoT-based Door Access System with Face Recognition. It serves several key purposes:
- Scope Definition: The Conceptual Framework aids in defining the scope and boundaries of the project, elucidating the specific goals, features, and constraints of the IoT-based Door Access System. This step ensures a comprehensive understanding of the project’s requirements and desired outcomes.
- Methodological Guidance: By outlining the overall project methodology, the Conceptual Framework directs the development team toward the selection of appropriate technologies and frameworks for integrating Face Recognition technology and IoT components. It helps in identifying the most suitable tools and protocols for creating a robust and secure access control system.
- User-Centric Design: The Conceptual Framework emphasizes a user-centric approach, ensuring that the IoT-based Door Access System is designed with a user-friendly interface for seamless enrollment and access control. It encourages the integration of features that prioritize user convenience and security, fostering a smooth and efficient user experience.
- Ethical and Security Considerations: By emphasizing ethical standards and security protocols, the Conceptual Framework ensures that the development process adheres to established norms and regulations, particularly in the context of privacy and data security. It supports the creation of an access control system that prioritizes user privacy and data protection, building trust and reliability among users and stakeholders.
By leveraging a well-defined Conceptual Framework, the development team can effectively navigate the complexities of the project, ensuring that the IoT-based Door Access System aligns with user requirements, technological advancements, and ethical standards, ultimately resulting in the creation of a secure and user-friendly access control solution.
Conceptual Framework Diagram
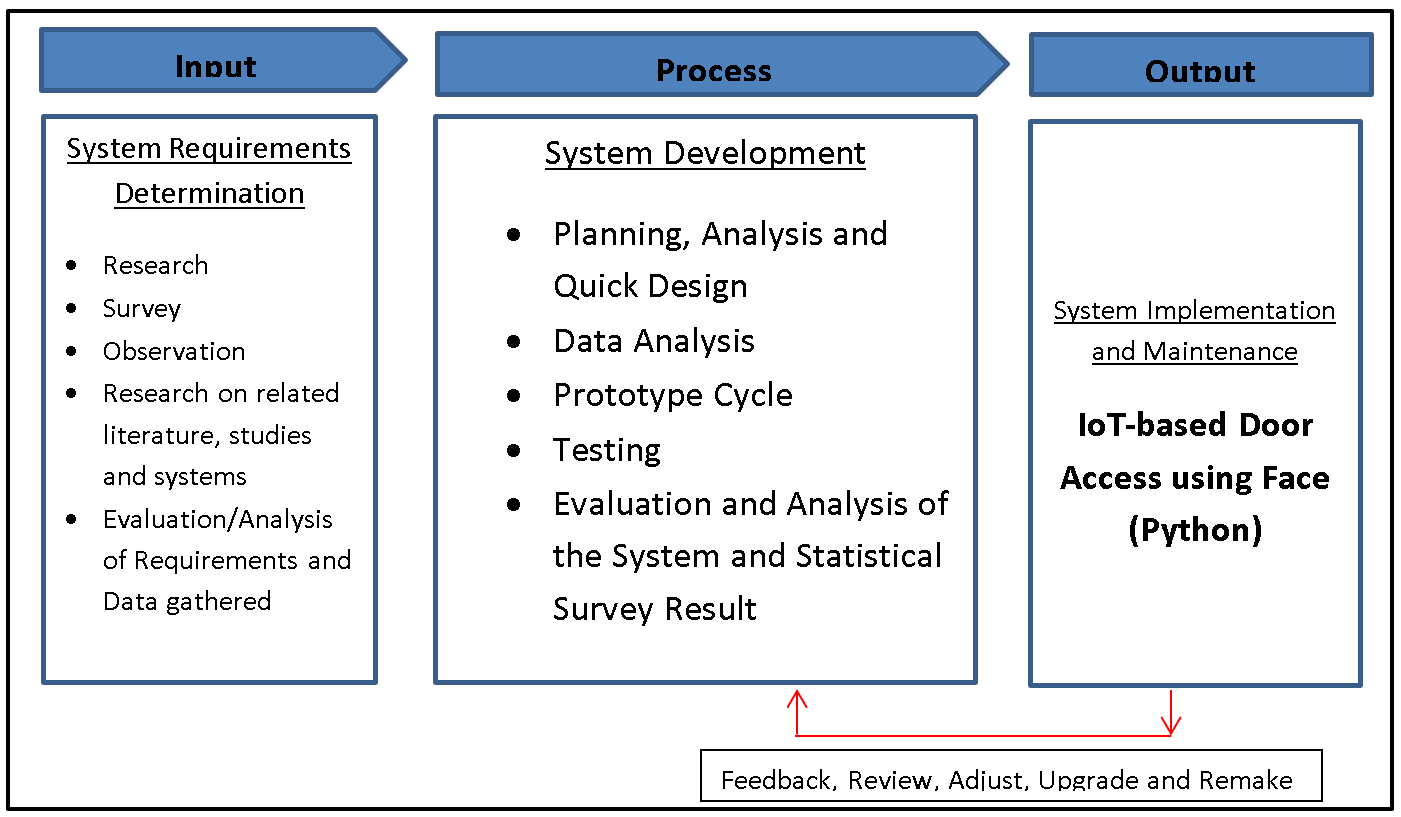
The image above depicts the project’s conceptual framework, entitled IoT-based Door Access using Face (Python). It is based on the input, process, and output (IPO) model.
Input
The input phase, known as the System Requirements Determination, constitutes the preliminary stage in the development of the IoT-based Door Access System with Face Recognition. This phase involves a comprehensive and systematic approach to gather and analyze critical information. Firstly, thorough research is conducted to delve into the latest advancements and methodologies in face recognition technology, IoT systems, and access control mechanisms. This extensive exploration enables the development team to comprehend the technical intricacies and challenges associated with the integration of these cutting-edge technologies, thereby aiding in informed decision-making throughout the development process.
Additionally, conducting surveys plays a pivotal role in collecting direct feedback and insights from prospective users, administrators, and security personnel. These surveys provide invaluable information regarding user preferences, expectations, and concerns related to access control systems. By understanding user requirements and expectations, the development team gains essential guidance in shaping the functionalities and user interface of the IoT-based Door Access System. Moreover, active observation and analysis of existing access control systems and security protocols in various environments offer practical insights into current challenges and best practices. This approach facilitates the identification of potential issues and areas for enhancement in access control systems, allowing the team to design a robust and dependable system that effectively addresses the identified concerns. Conducting a thorough review of related literature, studies, and previous projects associated with face recognition technology, IoT systems, and access control mechanisms further contributes to an enhanced understanding of industry trends and standards. This knowledge integration aids in the incorporation of best practices and innovative solutions into the development of the IoT-based Door Access System. Finally, the meticulous evaluation and analysis of the requirements and data collected from research, surveys, and observations establish the fundamental basis for defining the system’s key features, functionalities, and technical specifications. This analysis ensures the system’s alignment with user needs and project objectives, setting the stage for a comprehensive and user-centric development process.
Process
The process phase, which follows the System Requirements Determination, encompasses the systematic progression of the IoT-based Door Access System’s development, adhering to the Software Development Life Cycle (SDLC) principles. This phase involves several pivotal steps:
- Planning, Analysis, and Quick Design: The initial stage focuses on formulating a comprehensive plan outlining the system’s design, functionalities, and technical specifications. It involves a detailed analysis of the system requirements determined in the previous phase, leading to the creation of a quick design prototype that serves as a preliminary model for the subsequent development process.
- Data Analysis: This step involves the comprehensive analysis of the data collected during the initial phase, including user feedback, system requirements, and technical specifications. By conducting thorough data analysis, the development team gains valuable insights into the system’s operational requirements and the specific functionalities necessary to meet user needs and industry standards.
- Prototype Cycle: The prototype cycle involves the iterative development and refinement of the system’s prototype, allowing the development team to create a functional model that aligns with the project’s objectives and user requirements. This iterative process facilitates continuous improvements and enhancements to the system’s design and functionality, ensuring its effectiveness and user-friendliness.
- Testing: The testing phase is critical in evaluating the system’s performance and functionality under various simulated scenarios. It involves rigorous testing procedures to identify and rectify any potential glitches, vulnerabilities, or performance issues. Through comprehensive testing, the development team can ensure that the IoT-based Door Access System meets the highest standards of reliability, security, and performance.
- Evaluation and Analysis of the System and Statistical Survey Result: This final step involves the thorough evaluation and analysis of the fully developed system and the statistical survey results obtained during the testing phase. It includes a comprehensive assessment of the system’s overall performance, functionality, and user satisfaction, enabling the team to identify any areas for improvement and make necessary refinements to optimize the system’s efficiency and effectiveness. This detailed evaluation and analysis ensure that the IoT-based Door Access System meets the established standards and effectively addresses the identified user needs and project objectives.
Output
The output phase of the IoT-based Door Access System involves the crucial step of system implementation, where the fully developed system is prepared for deployment into the live environment. This phase encompasses several essential processes, including the installation of the system components, software deployment, and configuration of the hardware devices. These activities are carried out to ensure that the IoT-based Door Access System is seamlessly integrated into the operational environment, ready to perform its designated functions and cater to the access control requirements.
Furthermore, the system implementation process involves meticulous planning and execution to guarantee a smooth transition from the development phase to the live environment. This includes thorough testing of the system’s functionality in the real-world setting to validate its performance and reliability under actual usage conditions. Additionally, the installation of the IoT-based Door Access System in the live environment requires careful consideration of security protocols and data protection measures to safeguard sensitive information and ensure a secure access control mechanism.
Moreover, the process of system update or upgrade is crucial to ensure the longevity and relevance of the IoT-based Door Access System. Regular updates and upgrades facilitate the integration of the latest technological advancements, security patches, and feature enhancements, thereby enhancing the system’s performance, security, and user experience. This continuous improvement process guarantees that the IoT-based Door Access System remains at the forefront of technological innovation, providing users with an efficient, reliable, and secure access control solution.
Summary
The blog post on the Conceptual Framework of IoT-based Door Access Using Face Recognition introduces the systematic development process of an advanced access control system. It emphasizes the significance of the input phase, highlighting crucial steps like system requirements determination through research, surveys, observation, and data analysis. Furthermore, it provides insights into the subsequent process phase, following the SDLC principles, and explains the essential stages of system development, including planning, analysis, quick design, data analysis, prototype cycles, testing, and performance evaluation. The blog post also underscores the importance of the output phase, focusing on system implementation, deployment in live environments, and continuous updates and upgrades to ensure the sustained functionality and relevance of the system.
Readers are also interested in:
Face Recognition Application Database Design
You may visit our Facebook page for more information, inquiries, and comments. Please subscribe also to our YouTube Channel to receive free capstone projects resources and computer programming tutorials.
Hire our team to do the project.